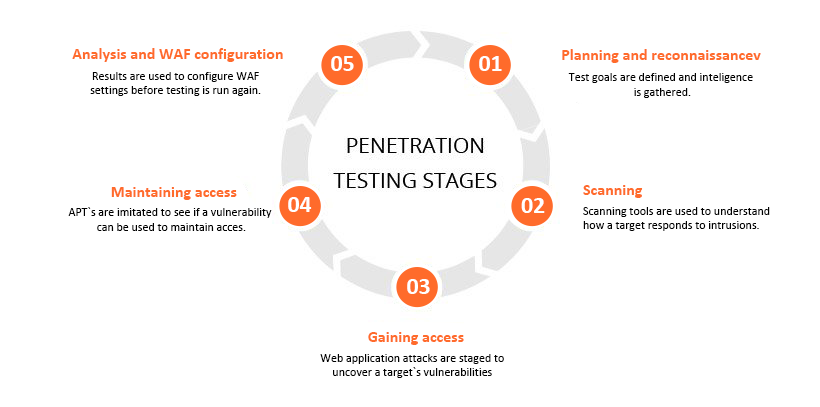
Penetration Testing
We perform apex quality penetration testing to assure that your website remains safe and secured from both external as well as internal threats. Our trainers actively analyze and evaluate any probabilities of potential risks attributing to flaws in hardware, software or in operations. We determine the feasibility of a specific set of attacks and its impact likely to be concerned business. Here we hack your website with your permission and find all related loopholes. We then precisely work on the loopholes and make your site perfectly secured. All followed methodologies are effective and we have our own unique way of dealing with security issues.
ITServerAdmin proactively conduct penetration test and evaluate the security of your IT infrastructure, which safely exploit vulnerabilities, including OS. We take care of the service and application flaws especially loose setups, and change all improper behavior. We would be managing the defensive mechanisms and adherence the security policies. Our penetration test will help to analyze the feasibility of systems and check any related issues and such incidents may affect the involved resources or operations.
We conduct penetration tests using manual or automated technologies for servers, web applications, networks and other potential points that are exposed to vulnerabilities. We would be testing compromised systems to check suitable exploits in other resources, specifically by trying it in the resources that have high level of security clearance. We would provide security vulnerabilities information to help IT and Network systems. We provide information about successful exploited security vulnerabilities through penetration testing is provided to IT persons to help to take strategic conclusions and prioritize related remediation efforts.
☑Determines the probability of a cyber attack
☑Assures whether the organization is functioning under the acceptable limit of security risks
☑Assesses the potential impact and repercussions of a succesful attack
☑Achieves regulatory compliance as per industry standarts(HIPPA, ISO/IEC 27001, PCI DSS etc)
☑Evaluates the efficiency of various security solutions
☑Prioritizes security risks as low, medium, and high severity
☑Uncovers poor internal security policies
☑Helps the incident response team perform better
☑Protects sensitive data
☑Improves business continuity
☑Maintains customer trust and brand image
☑Checks on organization`s preparedness to deal with unforeseen events
☑Plans defensive strategies for prevention against possible cyber-attacks, SQL injection attacks, DDoS attacks, and several others.